Types of Malware
What are Malwares?
Malicious + Softwares. These are the softwares like: Virus, Rootkit, Trojan, Worm, Spyware, Ransomware, Adware, Botnets and... that are developed by the black hat hackers for the purpose of stealing sensitive informations, financial details and destruction of systems.
. Virus
The most popular one is virus. it's a piece of code or an application that copies itself onto your computer or website without your knowledge. It attaches itself to another software and then it reproduces itself when we run that software. Mostly it spreads itself while sharing documents, files or software between computers. Viruses are in love to take down the main system files like windows/system32.
. Rootkit
it's the components of two words "Root", "Kit" where root is Linux term which is equal to Windows Administrator and Kit is Unix term which means softwares which are design to take root/Administrator privilege or control over targeted computer.
Rootkits are the hardest of all malware to detect because it works on kernel level and on the top of operating system with administrative privileges thus its difficult to remove from hard disk until the hard disk is fully wiped and install everything from scratch.
Rootkits are the hardest of all malware to detect because it works on kernel level and on the top of operating system with administrative privileges thus its difficult to remove from hard disk until the hard disk is fully wiped and install everything from scratch.
It's designed to allow other malicious softwares which are made to gather sensitive informations secretly.
Once a rootkit installs itself on your system, it will start at the same time as your PC. On top of that, by having administrator access, it can track everything you do on the device, scan your traffic, install programs without your consent, hijack your computer’s resources or enslave it in a botnet.

How rootkit spread itself
rootkits are just like any other applications that in order to be installed, it need a human effort (click).
Rootkits are usually having three components: the Dropper, loader, rootkit itself.
The dropper is the program or file that installs itself. you may meet the droppers from phishing emails or as a malicious file from compromised/evil website.
Droppers are not always executable programs; files such as PDF, Word documents can also be a trigger to install the rootkit the moment they opened.
Types of rootkit viruses
The severity of a rootkit infection can be measured depending on how deep into the system it goes.
Ring 3 infections are superficial since it only infects softwares like photoshop, Microsoft Office and similar SWs (SoftWares).
Ring 1 & 2 are a bit deeper layers so your drivers like sound card, video graphic card or NIC card will be infected.
Ring 0 in this layers it targets the Operating System that controls everything like BIOS. these level infections are very deep and it's very hard to remove because an antivirus works on ring 3 and and doesn't have full access to ring 0,1.
Kernel Rootkit
This level of rootkits are designed to even delete or replace the OS code and it adds its own code. these are very advanced and needs more technical knowledge to create.
If your lucky to face a buggy rootkit so it would be easier to detect and remove because it leaves behind a trail of clue for an antirootkit or antivirus.
Hardware or Firmware rootkit
Instead of software or OS, it targets the software which runs hardware components. In 2008, a European crime ring managed to infect card-readers with a firmware rootkit. This then allowed them to intercept the credit card data and send it overseas.
Hypervisor or Virtualized rootkit
These rootkits are new and advanced rootkits which takes advantages of new technologies.
A kernel rootkit boot up at the same time as OS but Hypervisor rootkit will be boot-up first and make a virtual machine and then boot-up the operating system.
Memory rootkit
Memory rootkits hide their selves in RAM of your computer and reduces the performance of your RAM memory by occupying the resources with all the malicious processes involved.
. Trojan/Trojan Horse
much like the myth and the movie Troy Trojan Horse clip from "Troy" - YouTube it shows itself a decent guy but actually he's rascal like Sean in American Pie movies.
A Trojan shows itself as a normal file that you download it but once you download it, it will be executed; the purpose of trojans are to steal your financial information like credit card number, master card etc.. it's also capable of doing DOS attack to make your resources unavailable to the requesters.
unlike viruses, Trojans doesn't need human interference to get executed it just need to be downloaded.


How do Trojans work?
You might think you’ve received an email from someone you know and click on what looks like a legitimate attachment. But you’ve been fooled. The email is from a cybercriminal, and the file you clicked on and downloaded and opened and it has gone on to install malware on your device.When you execute the program, the malware can spread to other files and damage your computer.
. Worms
Worms are hungry zombies which only be satisfied when there's nothing left to eat; the worst of all, it really enjoys Delivery; it gives birth every second like Bluefin Tuna fish which produces 10 million eggs per year.
We can say that Worms are the hunter of our computer files; it replicates itself and destroys the data on a computer until there's nothing left in Hard Drive.
We can say that Worms are the hunter of our computer files; it replicates itself and destroys the data on a computer until there's nothing left in Hard Drive.

. Spyware / Keyloggers
we can clearly get the image of what Spyware would be. yes it spies on our system and get reports back to it's developer or the hacker who developed it; every activity we do in our computer or phone and keystroke; by knowing the stroke it will know that what have you typed in a password field. Sometimes corporations and parents also uses it to know what their workers or children are doing.

. Ransomware
If you see a notification that your files and your drives are locked and encrypted or password protected and you cannot access to it until you transfer some amount of money in a bitcoin account, it's time to make a cold coffee for yourself my friend and take a nap because you need to calm down and find a way to jailbreak your innocent files and data by decrypting it which will take years to crack the password or pay the ransome or find the backup of your data.
. Adware
These are the types of malware that automaticaly displays unwanted advertisements. Clicking on one of these ads could redirect you to a malicious website. it's sometimes in the form of pop-ups and sometimes in the form of unclose-able window

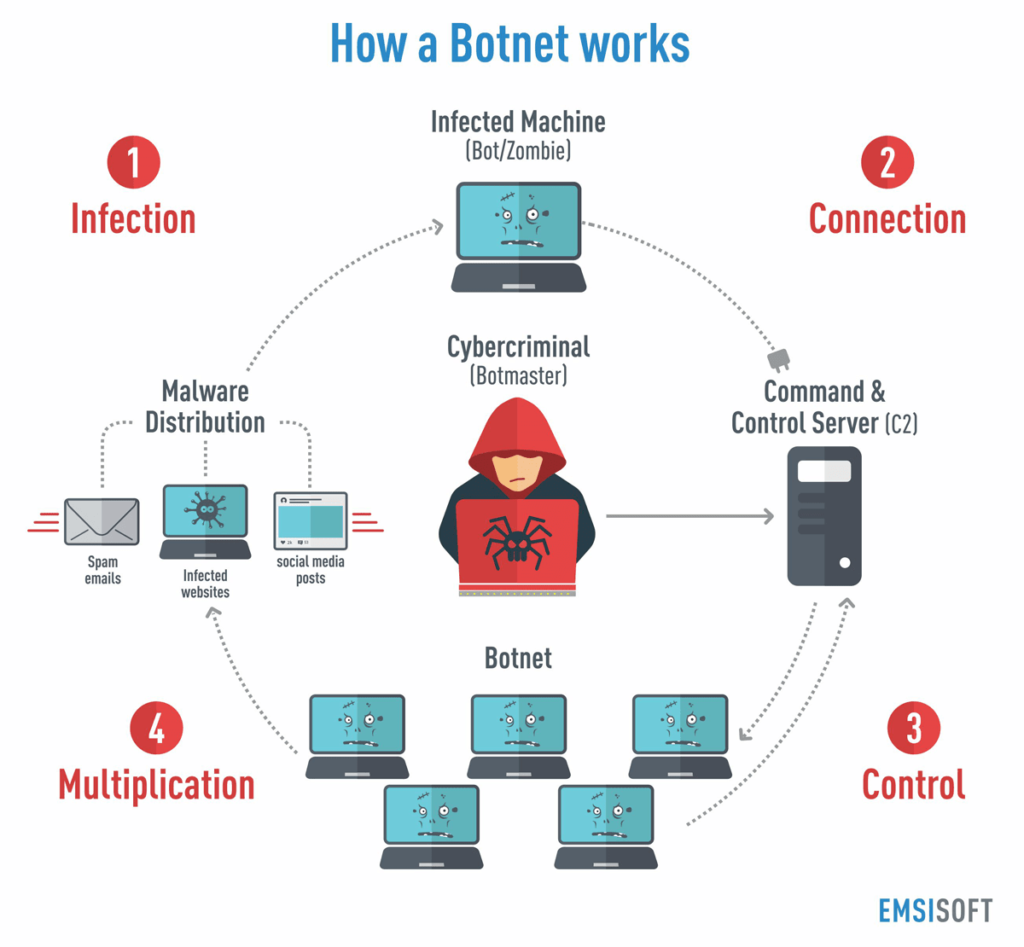
. Botnet / Bots
These are zombie computers or networks which are infected by the malware and controlled remotely by criminals, usually to perform DDOS attack on website to take it down.why a website server can't stop it? because all the request from every computer are counted as legitimate request that's why the server will be bombard by the request of infected computers.
. Backdoors
Backdoors are developed to open a backdoor into a system to provide a remote access to a network or single computer for hackers and later it will be used to enter a virus or Spam or any other malicious intentions.
It's typically covert method of bypassing normal authentication or encryption.
Backdoor installation could be achieved by taking the advantage of vulnerable web applications./https://cystory-images.s3.amazonaws.com/shutterstock_389659237.jpg)
Sign of virus or malicious software in your computer
one may not be familiar with the security threats of malware that compromises or invades the system, network or an organization; but be sure of these crystal clear signs that your system is compromised.
- You'll see plugins and strange files that you have no idea where it came from and you haven't installed it
- Slow performance of your browser/computer
- Endless pop-up and spam
- Unknown programs runs when you turn your computer on
- Your battery drains quickly
- High usage of CPU and loud fans
- Email being sent to your contact list automatically
- Absence or modified of files
- Antivirus or Firewall being turned off
- Frequent freezing of Applications/Operating System
- Change in files extension
While there are no full proof measure to avoid malwares but we can prevent and make a bit difficult to them to hack us.
How to Avoid Malwares
- Do not open any suspicious email but if you have opened it, do not click on any links or attachments in that mail and do not reply.
- If you find the email suspicious confirm the authenticity of it by checking with the sender through any communication medium.
- Enable automatic update that your OS and MS.Office programs get updated and.
- Microsoft Users should disable macros by defualt because a malware can also be in the form of macros.
- Uninstall third party programs like Java and Adobe Flash Player if its not required.
- Discontinue use of Windows XP and Windows 7 because Microsoft has stoped it's support for these two products and these two products are very easy to hack into.
- Backup your data in regular basis and keep it's copies offline and offsite.






Very useful work for our daily needs. Liked your hardwork
ReplyDelete